Phishing broadly refers to email attacks, which include fraudulent attempts by an attacker to obtain information about the target, in which the attacker sends an email which appears to be from a trusted source. In many phishing attempts, the email will ask the target to click a link, where they are prompted with a sign-in page. While the page appears to be genuine, by entering your information it hands those sign-in credentials over to the attacker. After an attacker has an email address/password combination from a target, they will attempt to use the same credentials to sign in to bank websites, email accounts, social media accounts and more.
There are a few different common methods attackers use to deceive targets: deceptive links, spoofing and social engineering. Attackers almost always use at least two of these methods to try to gain information (like sign-in credentials or financial information) from the target.
Deceptive Links
An example of a phishing email is pictured below. The branding, organized layout, and footer of the email all lend credibility to the appearance of the email. To the untrained eye, this email seems completely legitimate; however, there are a few elements here which raise red flags.
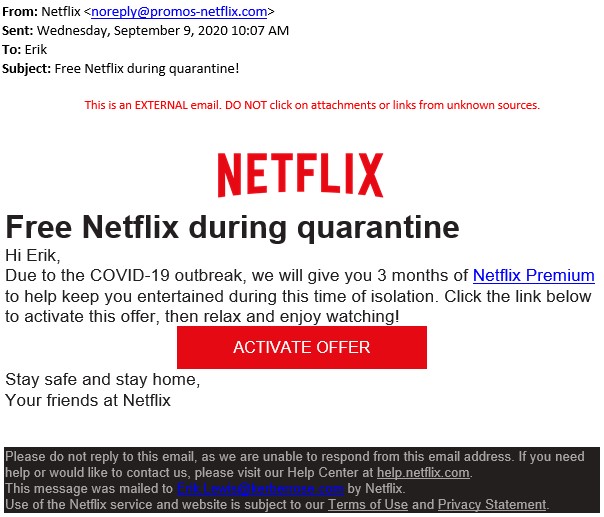
First, look closely again at the From: line—notice the sender’s address ends in “@promos-netflix.com.” A web address different from the company’s recognized address—in this case, netflix.com—is one indicator the email is not genuine (this is known as spoofing, which is covered in more detail below).
In this instance, another suspicious element of the message is the content itself. If the information contained in the email is suspiciously “too good to be true,” it very likely is not true.
A third, more well-hidden clue is in the ACTIVATE OFFER button itself. Most email apps allow the user to “hover” their cursor over a link in the body of an email and see the exact web address to which the link points. In this email, hovering over the link presents the web address pictured at left below.
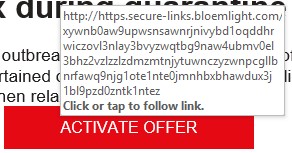 Here, the button points to an unfamiliar web address—one would expect a legitimate email from a company to point to that company’s website (in this example, it would be something like “https://netflix.com/...). This button pointing to a different website is another indication it is illegitimate.
Here, the button points to an unfamiliar web address—one would expect a legitimate email from a company to point to that company’s website (in this example, it would be something like “https://netflix.com/...). This button pointing to a different website is another indication it is illegitimate.Spoofing
As the previous example shows, spoofing refers to an attacker’s attempt to create a message which appears to come from a trusted source. Attackers can easily create an email address which looks like it comes from a legitimate company (as in the Netflix example above) or an individual who the target may know personally.
In cases where an individual’s email address is spoofed, the From: address will display the correct name, yet with a minor difference from the real address, such as a misspelling, or a substituted or added character. For example, if the real address is jane.smith@contoso.com, a spoofed address may appear as jame.snith@comtoso.com—a user skimming through emails may not notice the difference.
As demonstrated in the Netflix example above, the content of the email is another way to detect a spoofed email address. There are a couple questions which should be asked of any email appearing to come from a trusted source: Was I expecting to hear from this person? Are they asking me for information they shouldn’t need or I am not comfortable sharing with them? If either question returns a “no” answer, the email may not be legitimate.
Fortunately, in situations where an otherwise trustworthy sender is being spoofed, you may be able to initiate another line of contact to the apparent sender. For example, if the email appears to come from a trusted personal acquaintance, you could reach out to the person without replying to the email. For example, you could send a new email to the address you know is legitimate or ask them in person. Likewise, if the email appears to come from a company, reach out to someone you know personally at the company or call a customer service number found on the company website.
Social Engineering
A third method used by attackers is social engineering. In a social engineering attempt, the attacker’s message will attempt to influence the target using deception or emotional appeals. This is always used in conjunction with at least one of the other two methods discussed here. In the Netflix example above, the would-be target is baited into clicking a link by the allure of a free Netflix subscription.
Here is another example of a phishing email which includes all three of these phishing methods:
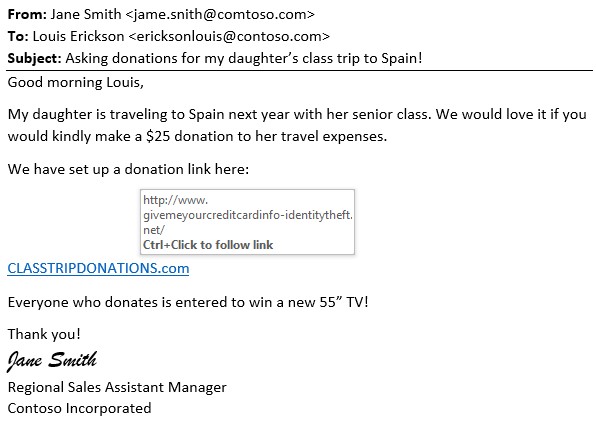
- Spoofing: the source address is cleverly misspelled, so it appears to come from a trusted source
- Social engineering: the email kindly asks the recipient to donate to a class trip, in exchange for entry to a drawing
- Link deception: the link points to a different address than what is spelled out in the link itself
Putting it all together
The most effective way to detect a phishing attempt is to always be skeptical. As displayed here, phishing attackers use a combination of clever (and often, devastatingly effective) methods to trick targets into handing over sensitive information. If any email appears suspicious, consider the following skeptical questions:
- Is this a source I trust?
- Did I expect to receive this email?
- Is this like other interactions I’ve had with this sender before?
- Are they asking for information I’m not comfortable sharing?
- Am I sure the source is actually who they say they are?
- Can I contact the apparent sender another way to verify the message?
For more information about securing your data from attackers, start a conversation at technology@kerberrose.com.








